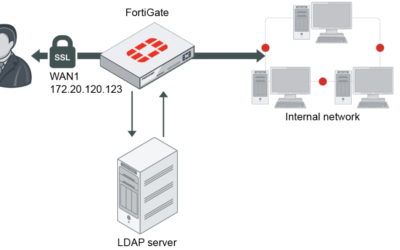
Domain Controller Migration from Windows Server 2012R2 -> Windows Server 2019
Windows Server 2012R2 is the seventh version of the Windows Server operating system by Microsoft, as part of the Windows NT family of operating systems. It is released in October 18 2013. There are many great features in Windows Server 2012R2 but as a time passed technology has been changed day to day. So, In…