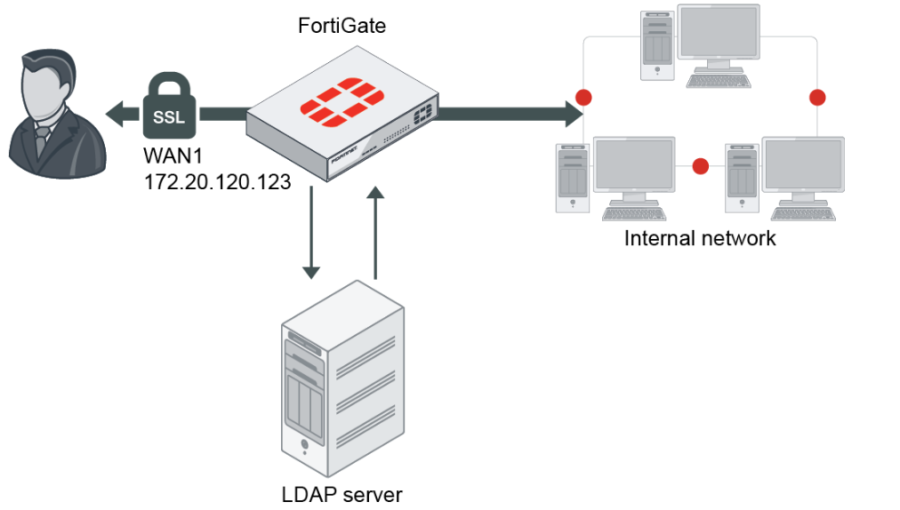
LDAP Authentication
LDAP stands for Lightweight Directory Access Protocol. LDAP authentication follows the client/server model. LDAP is particularly useful at helping organizations store and access usernames and passwords within their network and across applications. LDAP as a way to store and verify basic credentials whenever users are attempting to access an LDAP directory or LDAP-enabled systems and applications. LDAP is an essential tool in any business because of its interactions with the directory services — most commonly Microsoft’s Active Directory. As we’ll discuss shortly, LDAP is a means of communicating with Active Directory and connecting clients with the information they need that directory services actually store.
How LDAP Authentication Work?
A client sends a request for information stored within an LDAP database along with the user’s credentials to an LDAP server. The LDAP server then authenticates the credentials submitted by the user against their core user identity, which is stored in the LDAP database. If the credentials submitted by the user match the credentials associated with their core user identity that is stored within the LDAP database, the client is granted access and receives the requested information. If not, the client is denied access to the LDAP database.
Configuration LDAP Authentication on Fortigate.
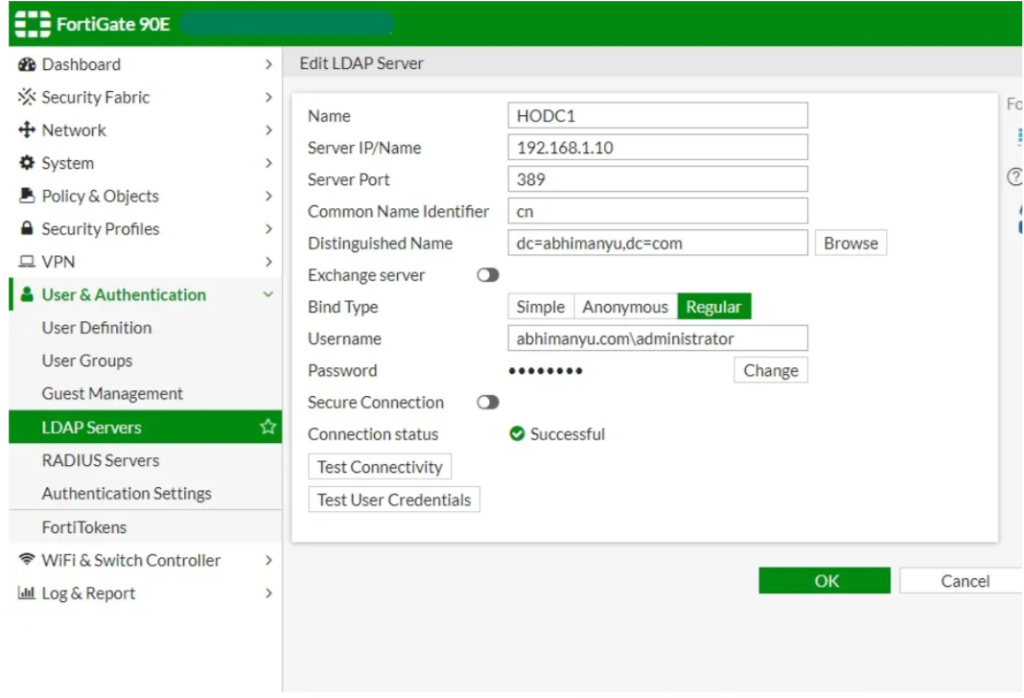
- Go to User & Device -> Authentication -> LDAP Servers and select Create New.
– Enter a Name for the LDAP server.
– In Server Name/IP enter the server’s FQDN or IP address.
– If necessary, change the Server Port number. The default is port 389.
– Enter the Common Name Identifier (20 characters maximum).
cn is the default, Cn is common name which is a display name (In reference to windows LDAP server).
– For Distinguished name, click on browse and select the main domain (Kindly select the domain once the Username and Password are entered as per step 8 and 9)
– In Bind Type, select Regular.
– In Username, enter the LDAP administrator’s name along with the domain (Ref. Screenshot below).
– In Password, enter the LDAP administrator’s password.
– Select OK
To import users from LDAP follow the below steps
1) Go to User & Authentication-> User Definition > Choose Remote LDAP User > Next.
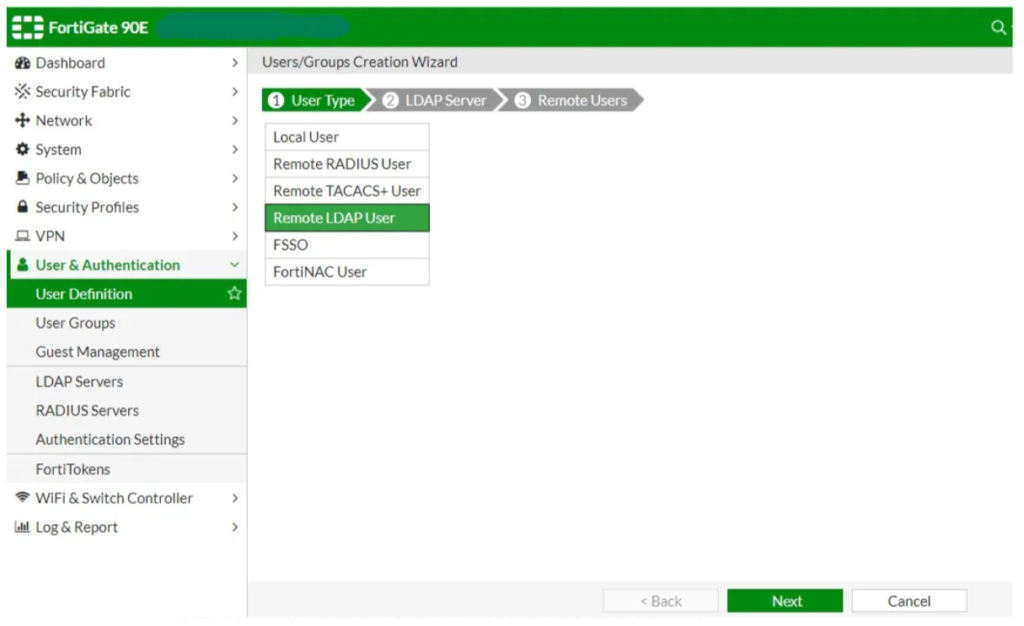
Now Choose you LDAP Server.
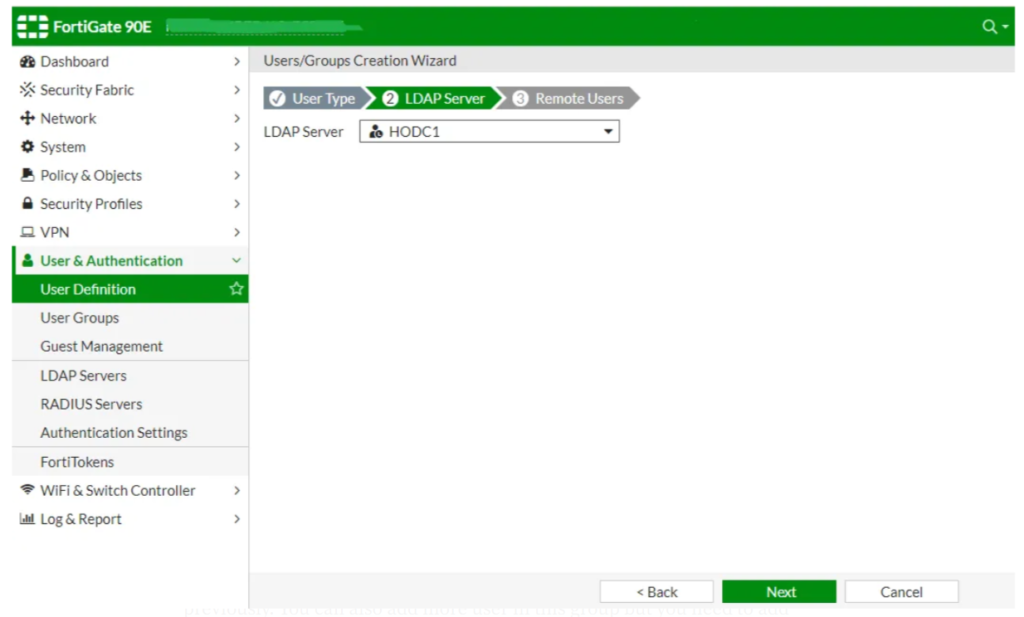
Here, You can see all the user from LDAP server select the user and Submit. (I have already added the user so there is no submit available.)
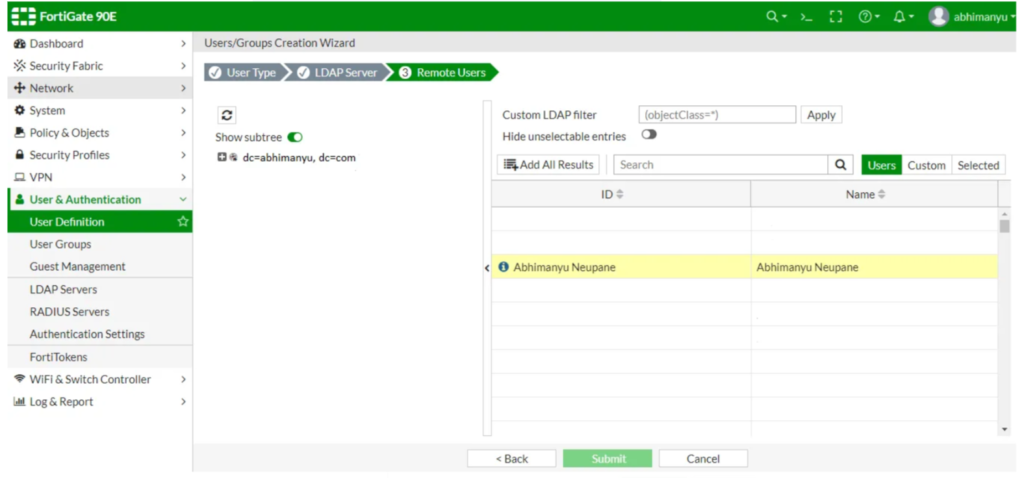
Here, we can create a group for certain department. I am creating a group Name IT where user is “Abhimanyu Neupane” which i have added previously. You can also add more user in this group but you need to add user from LDAP server to Fortigate. Now select the LDAP serve of Remote Server for this User.
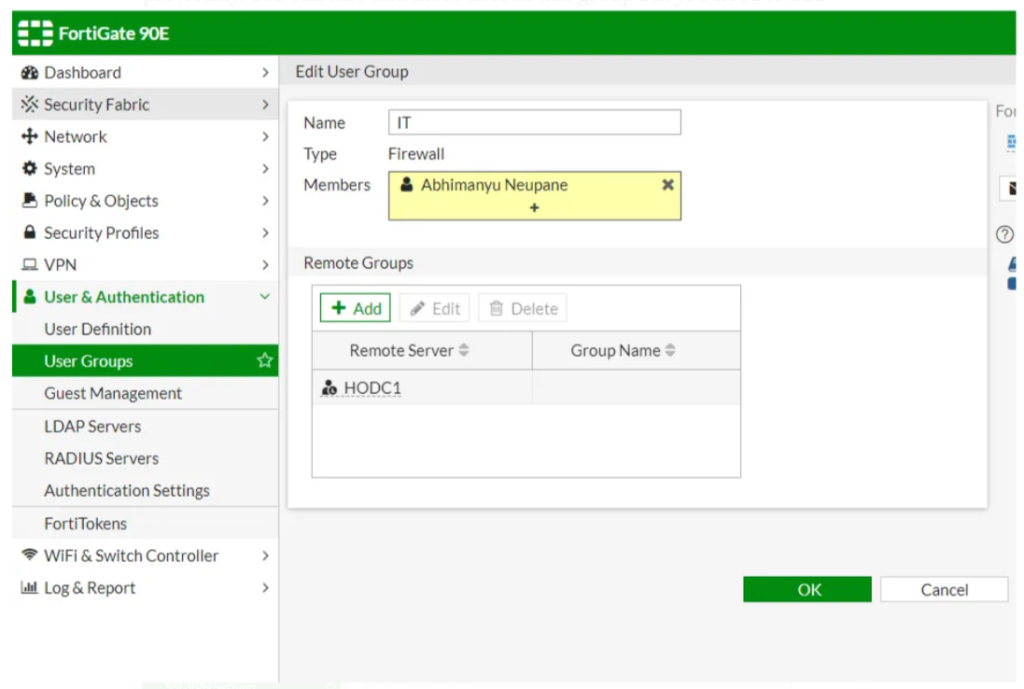
Click OK.
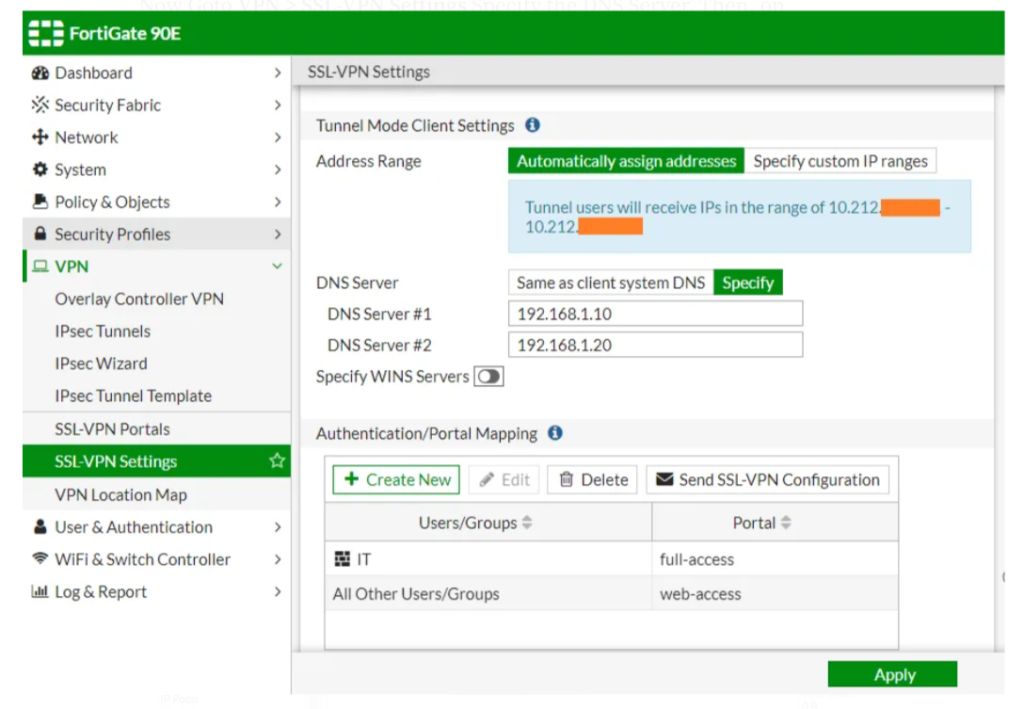
Now Goto VPN > SSL-VPN Settings Specify the DNS Server. Then, on Authentication. Create New and Add Group and select full-access. Then we can see the group or user and portal for that user or group. Select Apply.
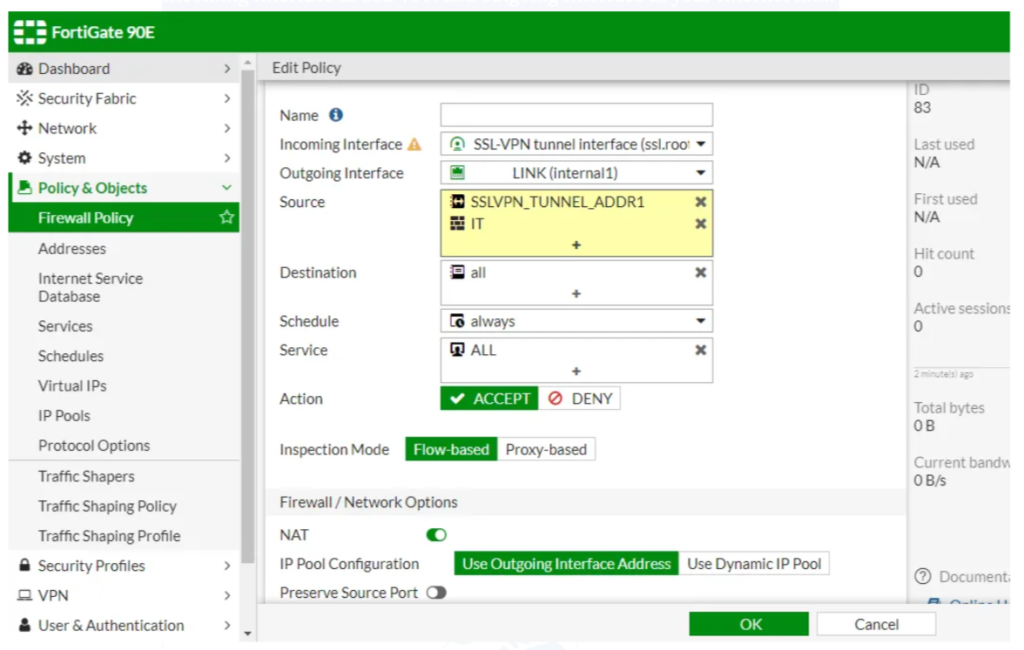
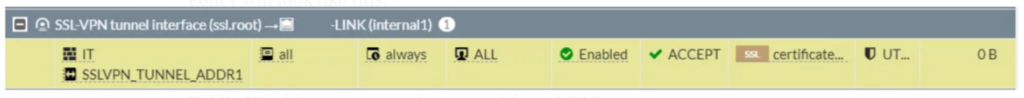
Now Goto Policy & Object > Firewall Policy > Create New. Now select the Incoming Interface as SSL-VPN and outgoing Interface as your Internet link. Add group on Source. Here i have added a IT group which i previously created. And, Address for SSL-VPN User.
Select Destination to ALL. NAT should be enable. Now, Click OK.
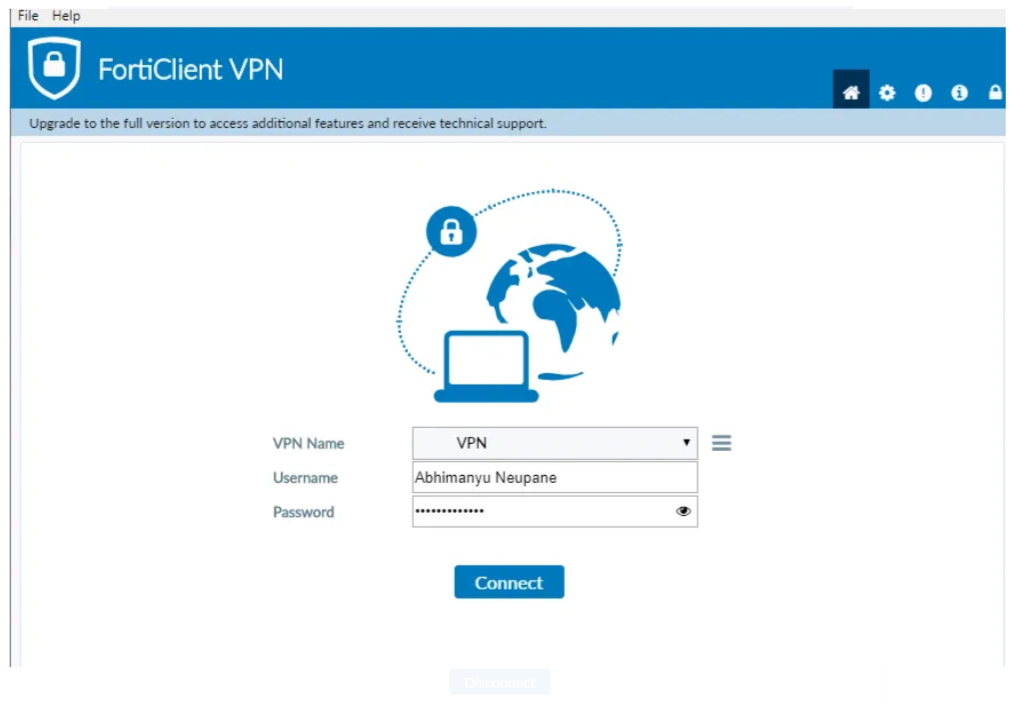
Now download the forticlient on you desktop, Create VPN by adding your Public IP, add username and password from LDAP server.
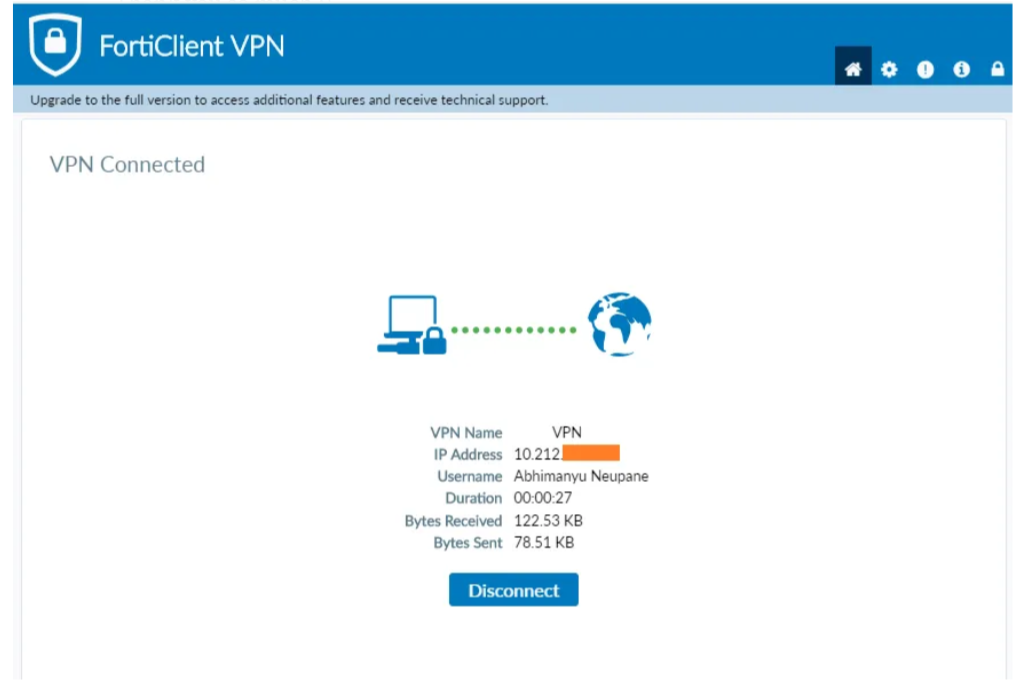
Now you successfully connect VPN using LDAP Authentication.
Thank you so much. 🙂
Comments are appreciated.