PAN-OS software implements IPsec VPNs as route-based tunnels, as opposed to policy-based designs.
- The determining factor of which traffic will be tunneled is the final destination of that traffic.
- It is easy to deploy and scale readily to large environments.
The firewall also interoperate which third-party, policy-based VPN devices:
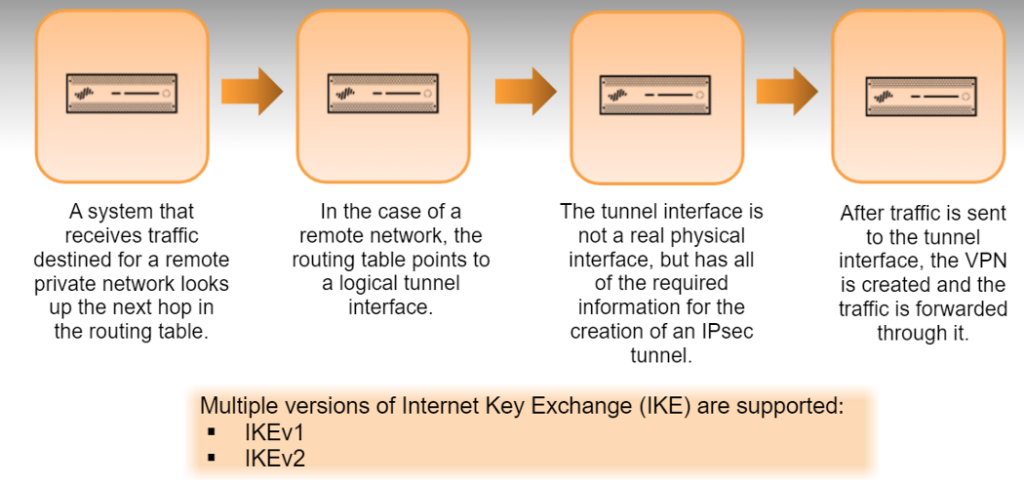
- A system that receives traffic destined for a remote private network looks up the next hop in the routing table, which is the standard procedure for traffic from another network.
- In the case of a remote network, the routing table points to a logical tunnel interface.
- The tunnel interface is not a real physical interface, but has all of the required information for the creation of an IPsec tunnel.
- After traffic is sent to the tunnel interface, the VPN is created and the traffic is forwarded thought it.
IKEv1 is the most commonly used version. IKEv2 primarily is used to meet the requirements of the Network Device Protection Profile, or NDPP, Certification, Microsoft Azure compliance, and/or Suite B support. “IKEv2 preferred mode” provides the ability to fall back to IKEv1 after five retries (about 30 seconds).
IKE Phase 1
In the first phase, the
- IKE protocol authenticates the firewalls to each other and sets up a secure control channel. It uses the IKE-Crypto Profile for IKE negotiation.
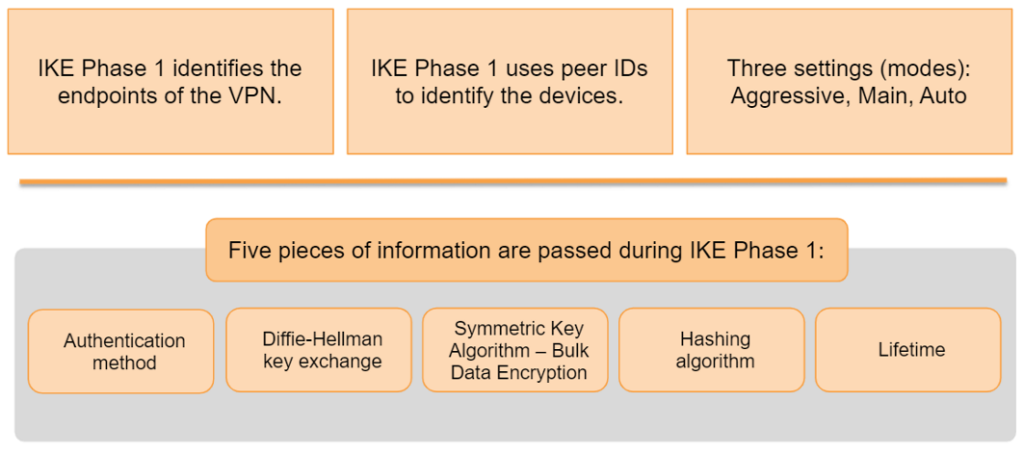
- IKE Phase 1 identifies the other firewall by a peer ID. Peer ID is just the public IP address or domain name of the other firewall.
- IKE Phase 1 provides authentication of the endpoints of tunnel and creates a secure channel of the next phase for VPN
The following information are passed during IKE Phase 1:
- Authentication Method
- Diffie-Hellman key exchange
- Symmetric Key Algorithm
- Bulk Data Encryption
- Hashing algorithm
- Lifetime
IKE Phase 2
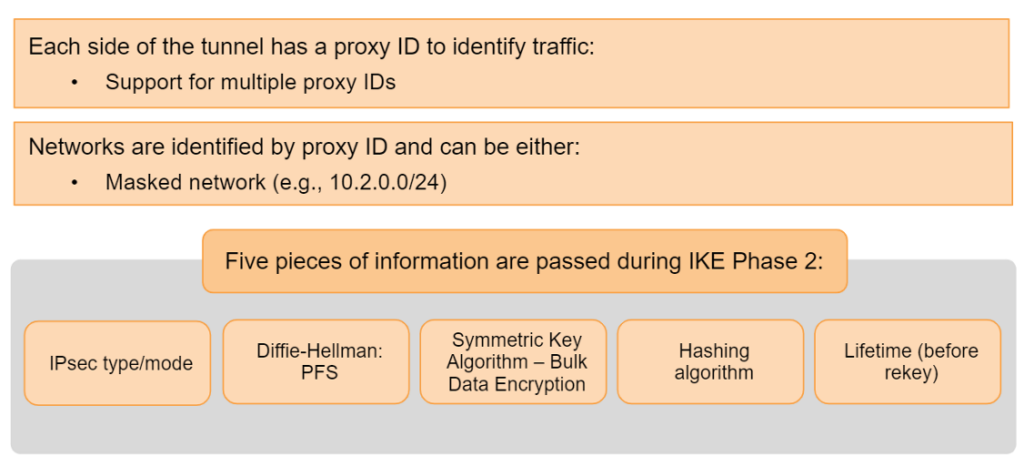
IKE Phase 2 creates the tunnel that encapsulate data traffic. IKE Phase 2 is concerned with data traffic that crosses the tunnel. Each side of the tunnel will have a proxy ID to identify the traffic it will be sending and what it expects to receive. The IDs either can be a specific network range or a generic network of 0.0.0.0/0. in either case, both sides need to know what the other side will be sending for the tunnel to work.
The following information are passed during IKE Phase2:
- IPsec type/mode
- Diffie-Hellman:PFS
- Symmetric Key Algorithm
- Bulk Data Encryption
- Hashing algorithm
- Lifetime (before rekey)
Note: You may be familiar with the idea of proxy ID under a different name: encryption domain. They are the effectively the same thing.